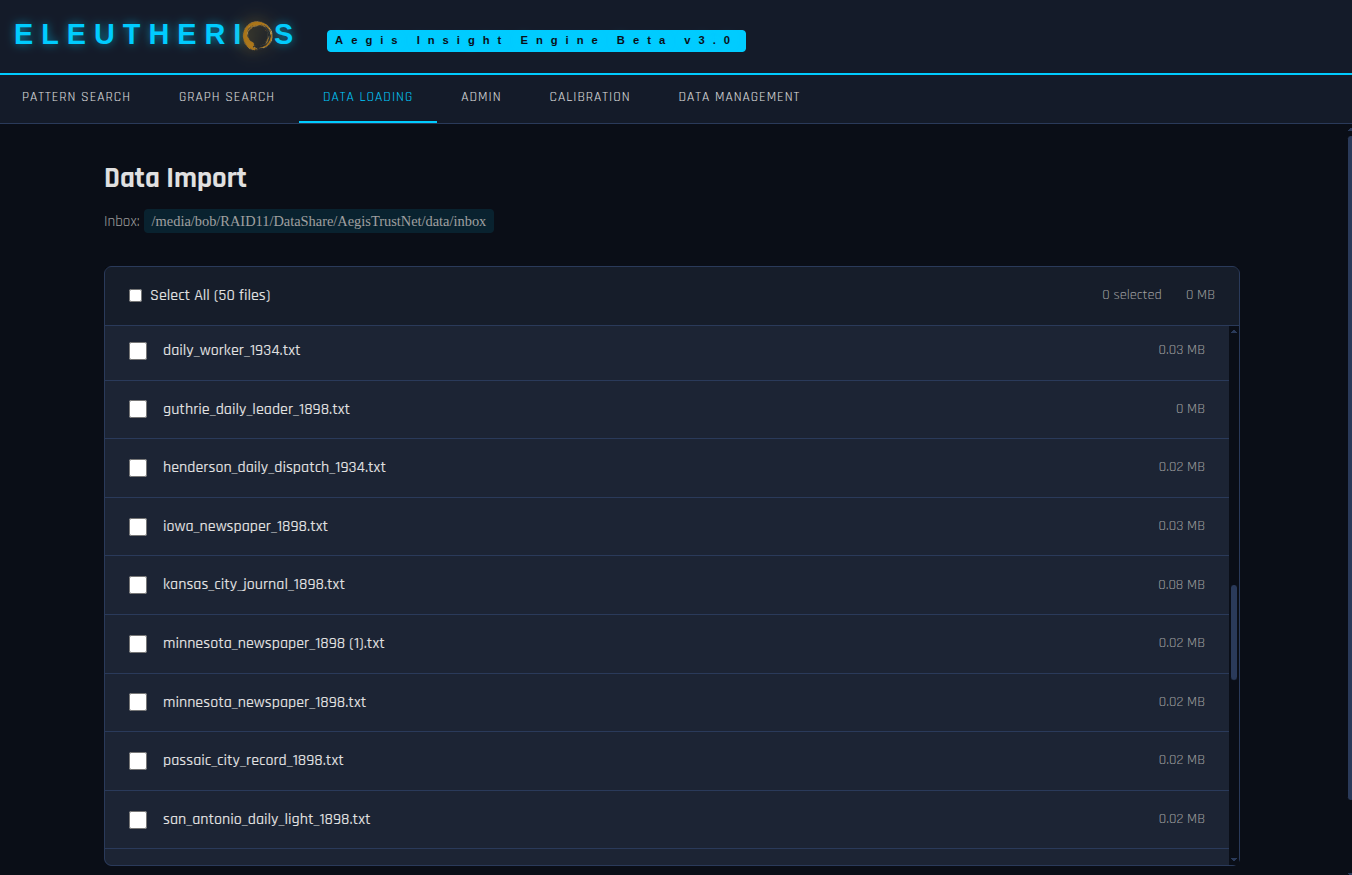
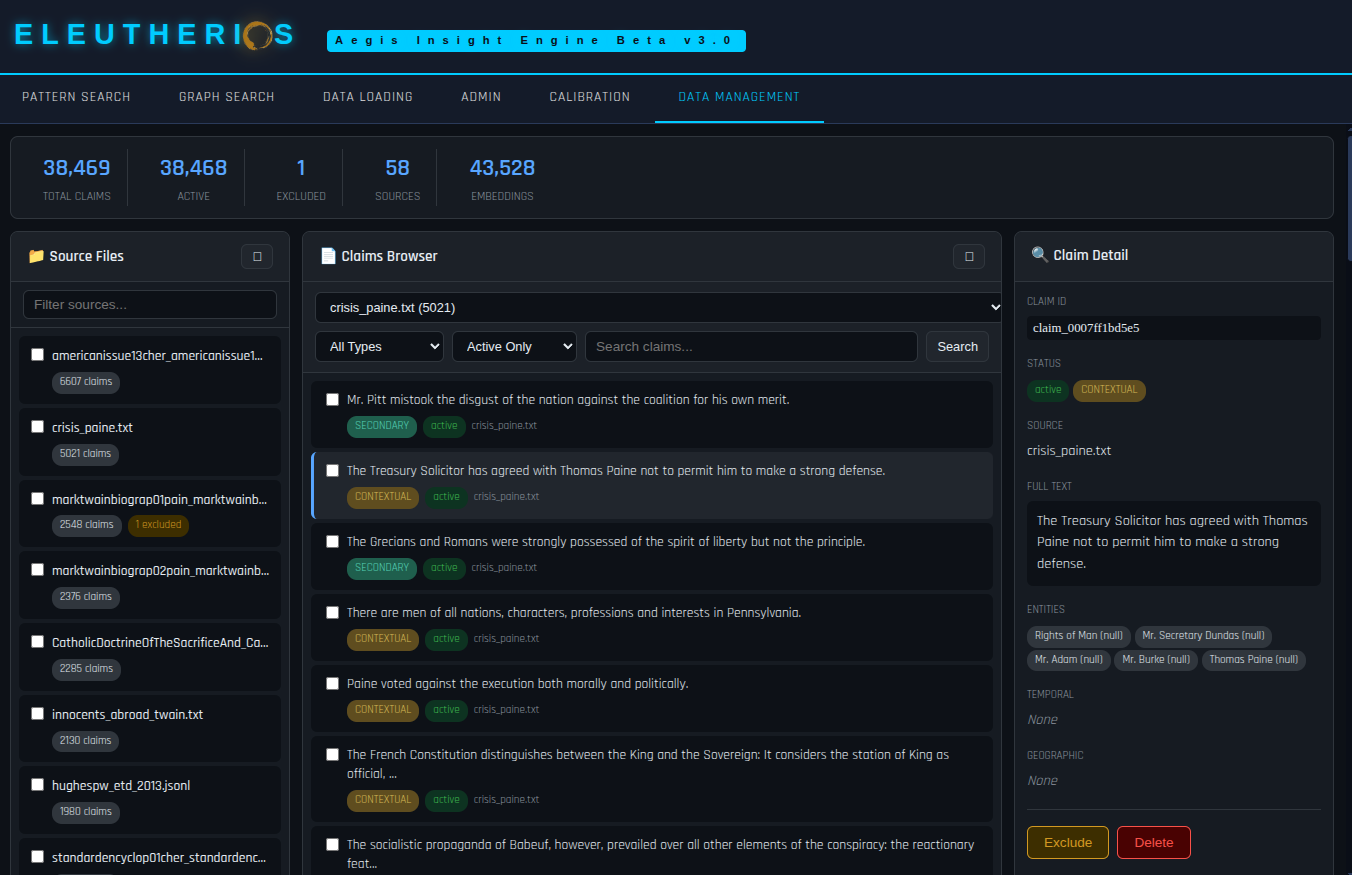
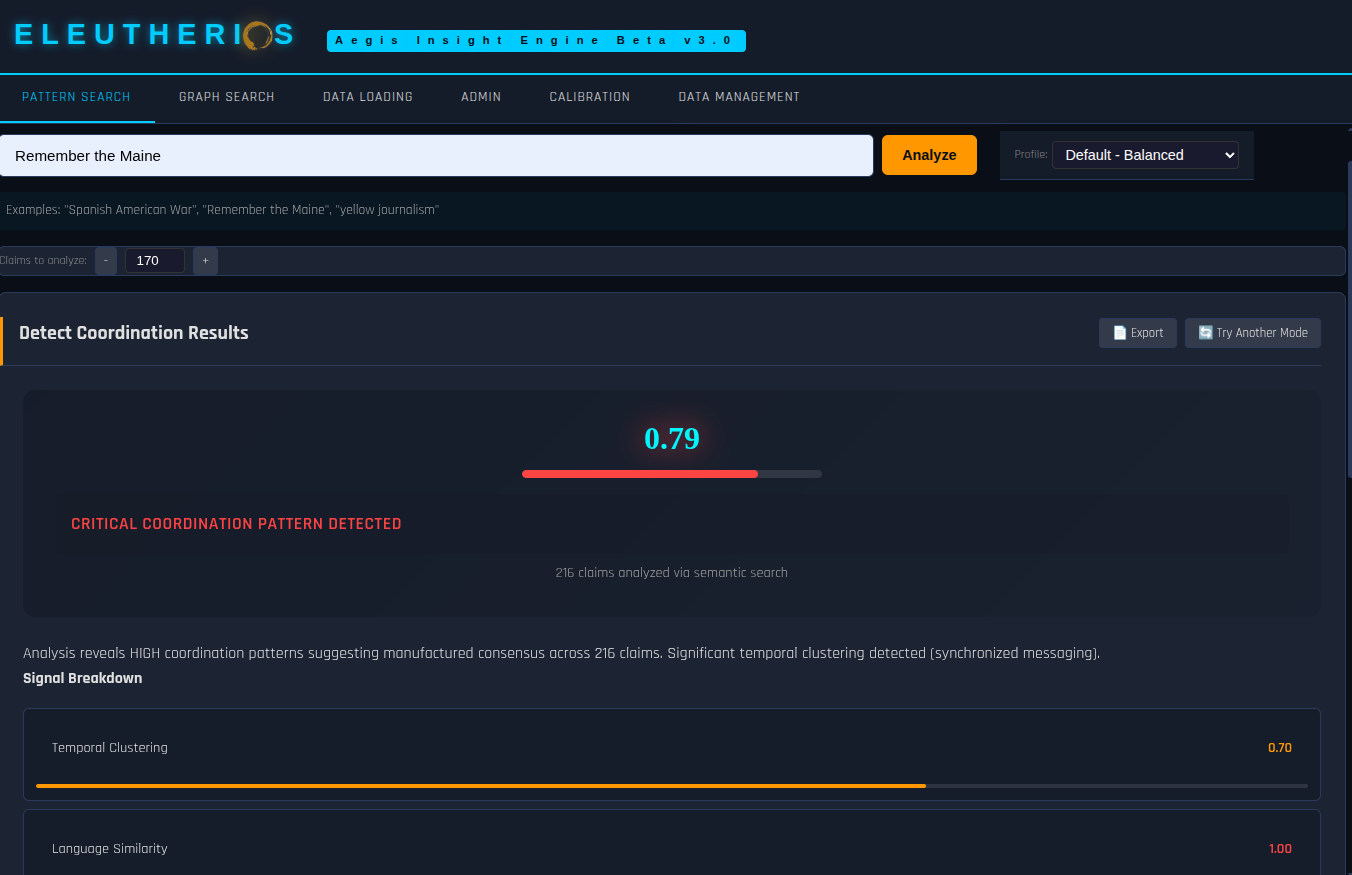
ARCHITECTURE
A two-stage pipeline: semantic retrieval finds relevant content, then epistemological analysis exposes the structure. Seven-dimensional extraction feeds a knowledge graph where detection algorithms identify patterns invisible to traditional search.